
- Offer Profile
- deister electronic is an innovative, family owned global business with more than 40 years experience in developing electronic and mechanical products for security and industrial automation. Widely acclaimed for our expertise and specialist implementation of RFID technology within practical applications, from key management, access control and long-range identification (AVI) to logistics and process control.
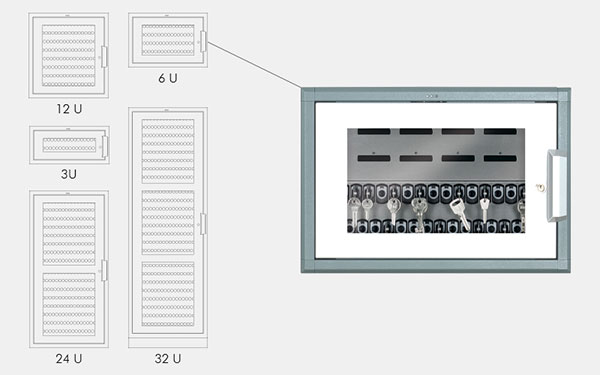
Key cabinets

-
Key handover management
Efficient storageManual key management can be time-consuming and nerve-wracking. Keys can easily get lost, causing frustration, and the search can be time-consuming and often unsuccessful. The more mechanical keys are in circulation, the harder it becomes to keep track of them. Manual key distribution, especially for security-critical buildings, rooms, commercial properties, industrial sites, fleet management, and vehicle fleets, can lead to significant administrative effort, security vulnerabilities, and high costs.
If you want to save yourself from this hassle and reclaim your valuable time, leaving behind the chaos of managing keys, you desire a clear overview and full control of your numerous keys, deister electronic offers efficient key management solutions. With electronic key management, user access to individual keys can be predefined and easily managed through the Commander Connect software.
All key withdrawals and returns are automatically documented and accessible at any time. The intelligent key cabinet, proxSafe, ensures a transparent, controlled key handover and efficient management of eight to several thousand keys.
Of course, your key storage can be customized to your requirements and the number and sizes of your key sets. Our cabinet models and flexible panels make it possible. Each key cabinet provides 24/7 access and is easy to set up and operate. Your key management experience: an absolutely secure solution for 100% control over all keys - and more resources for the essential tasks of the day.

maxx
-
Compact & elegant
Our compact proxSafe® key box maxx 6U with its space-saving, automatic roller shutter and elegant design guarantees an efficient key management for modern office environments. The electronic key box with robust steel housing offers enough space for single keys, narrow key bunches or even larger key bunches. Several key boxes can be combined and expanded with each other and can be easily operated with only one central terminal. All 3U keyPanels of the flexx series can be installed in the key box.
Thanks to our maintenance-free, robust keyTags with integrated RFID chips, all keys are firmly anchored in the maxx key box via slot locking, are not visible through the roller shutter and are thus double protected against manipulation.
To remove the key, the roller shutter of the key box automatically raises and the slot of the selected key slot lights up red. After removal, the roller shutter closes automatically and stops automatically if a hand is under the roller shutter.
flexx
-
Modular & flexible
The flexx key cabinet is available in five different sizes that can be individually combined according to the modular principle. In this way, small, compact systems from 16 key slots, or even large key depots with space for several thousand keys can be put together. The modular design offers maximum capacity in a small space and the possibility of adapting the system to the premises or expanding it at a later date. The cabinets can be individually equipped with the desired, flexible slot modules, called keyPanels, and can be easily extended or exchanged at short notice if required. Depending on the number and size of the key bundles, keyPanels are available with different slot densities. In addition, specific panels can be integrated for the controlled handover of ISO cards and radio devices.
To issue keys, the user identifies himself at the terminal, the door of the key depot can be opened and the key removed from the illuminated slot. Due to the slot interlocks, all keys are double-secured and can only be removed with the corresponding authorisation, even when the door is open.

smart
-
Compact & space-saving
The Smart 4 is a compact electronic key management system with 4 compartments that can manage single or multiple keys. Its design is based on user-friendliness: the user presents his badge and the system automatically releases only those keys which ithe user is actually authorised to remove.
The system offers operational security through a built-in battery backup and a local database that continues to function even in the event of network, server and power failures.
- Secure and compact
- Simple operation
- Remote key release through management software
Panels
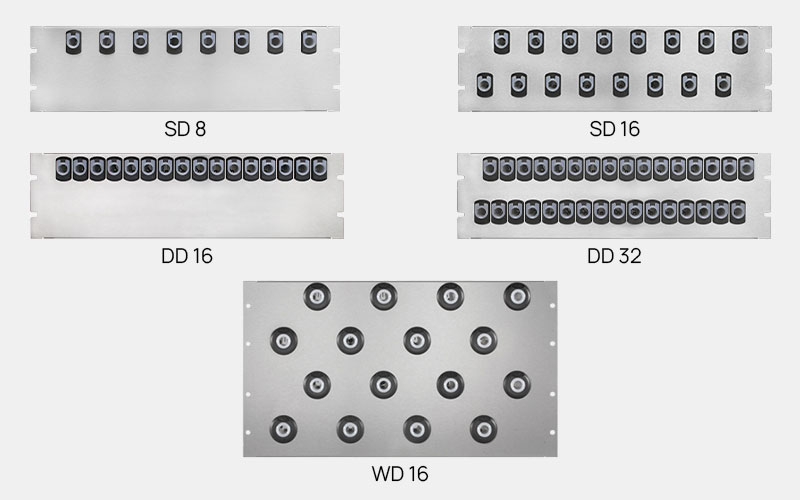
keyPanels
-
The right slot for every key
The flexx and maxx key cabinets can be individually equipped with slot modules called keyPanels. Due to the slot locking, all keys are firmly anchored in the cabinet and doubly protected against manipulation. Key access is only possible with the appropriate authorisation and identification. When keys are removed or returned, the slot of the selected keySlot lights up red.
Depending on the requirements, the keyPanels are available in different versions and differ in the number and spacing of the individual slots. For a large number of individual keys or small bunches of keys, our range offers keyPanels with up to 32 slots for maximum capacity. The keyPanels with generously arranged 8 or 16 slots offer plenty of space to store large bunches of keys neatly. With our modular and flexible panel concept, you can securely manage eight to several thousand keys, compile the key cabinets individually according to your needs and upgrade or expand your system at any time.

ISO 8 Panel
-
Safe storage for ISO cards
In addition to the keyPanels in the flexx key cabinet, ISO cards can also be stored securely using our ISO 8 panel. In each of the eight card slots, an ID card, credit card, petrol station card or access card in ISO 7810 ID-1 format can be stored in a tamper-proof and clearly arranged manner. For an increased level of security, the card slots can be optionally equipped with RFID and clearly displayed and managed with the Commander Connect software.
Terminals

C4+
-
Operating terminal with keypad and display
The proxSafe® C4+ terminal is suitable for all key management systems and electronic locker systems from the proxSafe® solution.
The operating terminal is supplied with an administrator ID card for setting up the system. Users can identify themselves via a credential card or by entering a PIN. The proxSafe® terminal enables quick and easy operation.
- Multi-technology reader for user identification
- Fast key return via 125 kHz reader
- Easy operation
- Intelligent power management
- Illuminated keypad and display

C6+
-
Operating terminal with touch display
The proxSafe® solution's C6+ touch terminal combines simple and intelligent operability with the display and operating functions of a colour 5.7" touch panel with capacitive touch screen. The C6+ terminal is compatible with all proxSafe® key management systems, as well as with all other locker systems. It comes with an administrator ID card to set up the system. Users can identify themselves via a transponder card or by entering a PIN. The optional multi-technology reader allows the use of many existing access control cards for user identification.
- Convenient operation via colour 5.7" touch panel
- Multi-technology reader for user identification
- Network and stand-alone capability
- Display of any characters (Unicode)
Accessories

keyTag
-
RFID key fob
keyTags are attached to each key, which are firmly connected to the key ring by a one-time seal. The keys on the keyTag can only be exchanged using special unsealing pliers and are therefore absolutely tamper-proof. An RFID chip is integrated in each keyTag, storing all information about the respective key.
When the key is inserted into the key cabinet, the key's data is transmitted via contactless identification, regardless of whether the key is dirty, oily or wet. This ensures that the keyTags will function reliably for a lifetime. Our keyTags are available in five colours. This allows you to quickly distinguish between different user groups or security levels by colour, for example, and to classify them clearly.

Unsealing pliers
-
The unsealing pliers are used for the authorized removal of one-time seals on keyTags and keyRings.
It has a large handle to separate the keyTags / keyRings from the keys with very little effort.
Smart Storage & Depot Systems
-
Manage equipment and valuables electronically
Optimize inventory and ensure availability
Are your resources being used optimally? It is easy to lose track of who used which device and when, and especially when and in what condition it was returned. proxSafe® creates an overview with handover control: The safe and controlled storage of objects and resources such as work equipment, tools, weapons or mail is always guaranteed. Removals as well as returns are automatically recorded electronically and access is only granted to authorized users. Access to the lockers is granted to the user via PIN, user card or fingerprint. With the Commander Connect software, access rights can be granted, time profiles defined and individual reports generated with just a few mouse clicks.
Deposit Systems
Self-service storage systems for temporary storage
The depot systems are ideal for the temporary storage of valuables, firearms or technical equipment. They reduce the administrative effort enormously, as they automatically document all deposits and removals and can carry out the registration of users completely independently aud automatically.
The modular design of the cabinets offer a great deal of flexibility in the design of the system, so that the appropriate compartment size can be planned for each item. The system can be completely self-contained or integrated with an online system, allowing for many more administrative functions, alarms and reporting.
- Automate the management of valuables and firearms
- Minimise administrative effort
- Improve traceability and documentation
- Large cabinet portfolio for flexibility in system design

locker S
-
Manage small valuables
The intelligent, electronic "locker" series offers great flexibility and scalability for the secure management and issuing of electronic devices and other valuables. Thanks to different locker sizes, a wide selection of operating terminals as well as central software control, they can be put together to suit almost any application.
With its compact form factor and up to 14 individual compartments, the locker S is ideally suited for storing smartphones, tablets and similar small electronic devices as well as valuables such as documents or bunches of keys in places where there is little space.
The individual compartments can be fitted with an RFID bracket that can be tailored to any device and features an integrated RFID reader. RFID chips installed in the item are thus automatically registered in the compartment when an item is removed and returned. Alternatively, the RFID chips can also be attached to the unit in the form of a keyTag dongle. This tag is inserted into a slot in the compartment. When the device is inserted or removed, the removal or return of the device is automatically registered and logged. This way, it is always clear which compartment holds which item and who had access to it last.
- Single or multiple removal
- RFID compartment monitoring (optional)
- Mechanical emergency opening in case of power failure
- Standalone mode with integrated backup battery in case of power or network failure

locker M
-
Manage medium sized valuables
The electronic locker systems of the "locker" series offer great flexibility and scalability for the secure management and transfer of electronic devices and other valuables. Thanks to various locker sizes, a wide selection of operating terminals and central software control, they can be put together to suit almost any application.
With its up to 12 individual compartments, the locker M easily stores laptops, large tablets and other electronic devices as well as files and tools. The locker M is also ideal for the automated management of service weapons, magazines and security equipment.
The individual compartments can be equipped with a receptacle adapted to the device with an integrated RFID reader. RFID chips installed in the item are thus automatically registered in the compartment when the item is removed and returned. Alternatively, the RFID chips can also be attached to the unit in the form of a keyTag dongle. This tag is inserted into a slot in the compartment. When the device is inserted or removed, the removal or return of the device is automatically registered and logged. This way, it is always clear which compartment holds which item and who had access to it last.
- Single or multiple removal
- RFID compartment monitoring (optional)
- Mechanical emergency opening in case of power failure
- Standalone mode with integrated backup battery in case of power or network failure

locker L
-
Manage large valuables
The intelligent, electronic "locker" series offers great flexibility and scalability for the secure management and issuing of electronic devices and other valuables. Thanks to different locker sizes, a wide selection of operating terminals as well as central software control, they can be put together to suit almost any application.
The largest locker column in the series - locker L - offers eight medium, six large or four extra-large compartments for secure storage of even bulky valuables. There is enough space in the compartments for large laptops, test equipment, cases or special tools.
The individual compartments can be fitted with an RFID bracket that can be tailored to any device. RFID chips installed in the item are thus automatically registered in the compartment when an item is removed and returned. Alternatively, the RFID chips can also be attached to the unit in the form of a keyTag dongle. This tag is inserted into a slot in the compartment. When the device is inserted or removed, the removal or return of the device is automatically registered and logged. This way, it is always clear which compartment holds which item and who had access to it last.
- Single or multiple removal
- RFID compartment monitoring (optional)
- Mechanical emergency opening in case of power failure
- Stand-alone mode with integrated backup battery in case of power or network failure

locker F12
-
Manage valuables in portrait format
The proxSafe® flexx locker F12 is an electronic locker system with vertically aligned compartments. These are particularly suitable for storing and managing items and equipment in vertical format.
Each locker can be controlled individually. A user can also open several lockers in one withdrawal/return process to withdraw/return several items at once.
- Compartments in portrait format
- Single or multiple removal
- RFID compartment monitoring (optional)
- Mechanical emergency opening in case of power failure
- Standalone mode with integrated backup battery in case of power or network failure
Terminals

C4+
-
Operating terminal with keypad and display
The proxSafe® C4+ terminal is suitable for all key management systems and electronic locker systems from the proxSafe® solution.
The operating terminal is supplied with an administrator ID card for setting up the system. Users can identify themselves via a credential card or by entering a PIN. The proxSafe® terminal enables quick and easy operation.
- Multi-technology reader for user identification
- Fast key return via 125 kHz reader
- Easy operation
- Intelligent power management
- Illuminated keypad and display

C6+
-
Operating terminal with touch display
The proxSafe® solution's C6+ touch terminal combines simple and intelligent operability with the display and operating functions of a colour 5.7" touch panel with capacitive touch screen. The C6+ terminal is compatible with all proxSafe® key management systems, as well as with all other locker systems. It comes with an administrator ID card to set up the system. Users can identify themselves via a transponder card or by entering a PIN. The optional multi-technology reader allows the use of many existing access control cards for user identification.
- Convenient operation via colour 5.7" touch panel
- Multi-technology reader for user identification
- Network and stand-alone capability
- Display of any characters (Unicode)
Weapon management

-
Self-service storage systems for temporary storage
The depot systems are ideal for the temporary storage of valuables, firearms or technical equipment. They reduce the administrative effort enormously, as they automatically document all deposits and removals and can carry out the registration of users completely independently aud automatically.
The modular design of the cabinets offer a great deal of flexibility in the design of the system, so that the appropriate compartment size can be planned for each item. The system can be completely self-contained or integrated with an online system, allowing for many more administrative functions, alarms and reporting.
- Automate the management of valuables and firearms
- Minimise administrative effort
- Improve traceability and documentation
- Large cabinet portfolio for flexibility in system design

locker S
-
Manage small valuables
The intelligent, electronic "locker" series offers great flexibility and scalability for the secure management and issuing of electronic devices and other valuables. Thanks to different locker sizes, a wide selection of operating terminals as well as central software control, they can be put together to suit almost any application.
With its compact form factor and up to 14 individual compartments, the locker S is ideally suited for storing smartphones, tablets and similar small electronic devices as well as valuables such as documents or bunches of keys in places where there is little space.
The individual compartments can be fitted with an RFID bracket that can be tailored to any device and features an integrated RFID reader. RFID chips installed in the item are thus automatically registered in the compartment when an item is removed and returned. Alternatively, the RFID chips can also be attached to the unit in the form of a keyTag dongle. This tag is inserted into a slot in the compartment. When the device is inserted or removed, the removal or return of the device is automatically registered and logged. This way, it is always clear which compartment holds which item and who had access to it last.
- Single or multiple removal
- RFID compartment monitoring (optional)
- Mechanical emergency opening in case of power failure
- Standalone mode with integrated backup battery in case of power or network failure

locker M
-
Manage medium sized valuables
The electronic locker systems of the "locker" series offer great flexibility and scalability for the secure management and transfer of electronic devices and other valuables. Thanks to various locker sizes, a wide selection of operating terminals and central software control, they can be put together to suit almost any application.
With its up to 12 individual compartments, the locker M easily stores laptops, large tablets and other electronic devices as well as files and tools. The locker M is also ideal for the automated management of service weapons, magazines and security equipment.
The individual compartments can be equipped with a receptacle adapted to the device with an integrated RFID reader. RFID chips installed in the item are thus automatically registered in the compartment when the item is removed and returned. Alternatively, the RFID chips can also be attached to the unit in the form of a keyTag dongle. This tag is inserted into a slot in the compartment. When the device is inserted or removed, the removal or return of the device is automatically registered and logged. This way, it is always clear which compartment holds which item and who had access to it last.
- Single or multiple removal
- RFID compartment monitoring (optional)
- Mechanical emergency opening in case of power failure
- Standalone mode with integrated backup battery in case of power or network failure

WDC 8
-
Store long guns safely and securely
Securely store weapons, ammunition and other security equipment in individual, locked drawers. Restrict access to each item to authorised personnel only at specific times and maintain a real-time electronic audit trail of who takes what and when. All weapons can be fitted with RFID transponders to automatically track removals and returns.
Our products include a wide range of lockers and cabinets designed to safely store your weapons and equipment. Store handguns, carbines and rifles - and manage them all in one system. Made in Germany. Our renowned quality standards guarantee
a very long service life and reliable use.- Automated logging of all withdrawals and returns
- Secure access via access control card or PIN
- Individual storage
- Notifications if your items are not returned
- System access can be limited to working hours
Terminals

C4+
-
Operating terminal with keypad and display
The proxSafe® C4+ terminal is suitable for all key management systems and electronic locker systems from the proxSafe® solution.
The operating terminal is supplied with an administrator ID card for setting up the system. Users can identify themselves via a credential card or by entering a PIN. The proxSafe® terminal enables quick and easy operation.
- Multi-technology reader for user identification
- Fast key return via 125 kHz reader
- Easy operation
- Intelligent power management
- Illuminated keypad and display

C6+
-
Operating terminal with touch display
The proxSafe® solution's C6+ touch terminal combines simple and intelligent operability with the display and operating functions of a colour 5.7" touch panel with capacitive touch screen. The C6+ terminal is compatible with all proxSafe® key management systems, as well as with all other locker systems. It comes with an administrator ID card to set up the system. Users can identify themselves via a transponder card or by entering a PIN. The optional multi-technology reader allows the use of many existing access control cards for user identification.
- Convenient operation via colour 5.7" touch panel
- Multi-technology reader for user identification
- Network and stand-alone capability
- Display of any characters (Unicode)
Acces control
-
The right solution for every door
doorLoxx® is our comprehensive access control system and provides an easy and cost-effective way to switch from a conventional locking system to a fully-fledged electronic access control system. The extensive product portfolio always offers the optimal solution for every type of door.
Important high-traffic doors such as the main entrance are controlled with an online reader and controller. Office doors and meeting rooms can be managed at the click of a mouse using offline cylinders and electronic fittings. All other conventional keys are automatically managed in our electronic key cabinets.
This means that every door in the building can be integrated cost-efficiently and according to the requirements whilst being manageable via software.
deister credentials offer the highest level of security and use the latest secure MIFARE® DESFire technology with customised CryptoKey handling.
Online Reader

Access control readers
-
One reader, all technologies
The timeless design provides a high-quality look and deister electronic's proven reading performance ensures fast and smooth operation. The readers are available in three different shapes to match the available space at the door. The reader's LEDs clearly indicate the status to the user. Even users with a red/green deficiency can recognise the status of the reader based on the LED positions. The readers feature a replaceable cover. Even after many years of use, you can make it look like brand new just by replacing the reader cover.
In addition to proven reading technologies such as MIFARE® Classic and MIFARE® DESFire, Bluetooth® and NFC™ are also supported. The readers have an open interface (Triple Technology™) to retrofit existing or future technologies, so you remain future-proof with the Infinity Readers™.
- Highest quality
- Low power consumption
- Remote firmware update
- Triple Technology™
- Available in two colours (Cosmic Black & Astral Grey)
- Interchangeable cover

Keypad readers
-
For cards and PINs
The keypad readers have a high-quality keypad with backlit keys and are available in three designs. The separately arranged LEDs clearly indicate the status to the user and the keypad provides haptic, visual as well as acoustic feedback. The reader's LEDs clearly show the status to the user. The keypad provides additional haptic, visual and acoustic feedback. Even users with a red/green deficiency can recognise the status of the reader based on the LED positions. The readers feature a replaceable cover. Even after many years of use, you can make it look like brand new just by replacing the reader cover.
Like the PRx access readers, the KPx keypad readers have an open interface (Triple TechnologyTM) to retrofit existing or future technologies.
- Highest quality
- Low power consumption
- Remote firmware update
- High-quality keypad with illuminated keys
- Triple TechnologyTM
- Available in two colours (Cosmic Black & Astral Grey)
- Replaceable cover

Flush-mounted readers
-
Our technology, your design
Our PRx 4 flush-mounted reader fits into any conventional flush-mounted box and can therefore be concealed. Whether you want to integrate it into other devices or install it with its own housing to match your design - there are no limits to your creativity.
- Highest quality
- Compact design suitable for conventional flush-mounted boxes
- Low power consumption
- Remote firmware update
- Triple TechnologyTM
Offline reader

Electronic cylinder
-
Easy to upgrade
Just like a mechanical cylinder, the electronic cylinder can be installed in just a few steps. No drilling or other modifications to the door are required because the design is identical. The basic cylinder bodies can be ordered in five different installation lengths, including a half cylinder, and can also be adjusted in length directly during installation using spacers, meaning that the length can be adjusted in 5 mm steps from 30/30 to 45/75.
- Installation length can still be adjusted during installation
- Best quality - Made in Germany
- Fast reading speed

Electronic door fitting
-
Suitable for every door
The electronic fitting suits any door with its slim and simple design. The handle can be selected from four different models, depending on its use on solid or tubular frame doors. For mounting, the same drill holes as for a conventional fitting can be used.
The cover plate allows the parallel use of the existing cylinder for secure door locking or the elegant covering of the cylinder opening. The exchangeable cover plate allows adaptation to doors with different distances between handle and cylinder. The Digital Handle adapts perfectly to any door.
- Suitable for every door
- Slim and elegant design
- Additional mechanical locking cylinder (optional)
- Simple battery change

Electronic lock
-
Design meets security
The electronic motor lock has been developed for self-locking locks and combines security with design. The simple design can be discreetly combined with the design of the door handle and offers maximum freedom in the choice of shape and colour.
In addition, the electronic lock offers more security because neither damage nor forcible removal of the housing or electronics allows access to the lock mechanism inside the door.
- Maximum freedom for design
- More security
- Different designs to suit every door

Electronic cabinet lock
-
Secure storage of valuables in lockers or wardrobes - with the reliable and electronic locker and furniture lock from deister electronic. The elegant and timeless electronic lock does not require any cables, can be installed quickly and is easy to manage thanks to our Commander Connect software. Connecting the lock and integrating it into professional building and asset management software is therefore no problem at all.
- Available with different levers
- Attractive design, suitable for many office furniture, lockers and wardrobes
- Easy to assemble

Digital Safe
-
The battery-operated Digital Safe is a rugged key safe for outdoor and indoor use. Its weatherproof IP65 housing is suitable for any weather. The Digital Safe is opened contactlessly with an access card or via an app - the reading technology can be freely selected and all popular reading technologies such as MIFARE®, NFC™ or Bluetooth® are supported. This means that the Digital Safe can also be seamlessly integrated into an existing access control system and can be opened with the same credentials. The Digital Safe can also be flush mounted, providing the best possible mechanical protection. Weather impacts are also minimised by this type of installation.
- 70 mm diameter
- Enough space for ISO cards and large bunches of keys
- Independent of local IT infrastructure
- Standalone capable
- Weatherproof IP65 metal housing
- Content monitoring

WCU 2 Offline door control
-
Reader with integrated door control
The WCU 2 door control module is a reader with integrated inputs and outputs. It only requires a power supply, but is otherwise integrated into the system like an electronic cylinder.
Wherever an existing online reader is to be replaced and the functionality of an electronic cylinder is not sufficient, the WCU 2 is the ideal solution.
- Integration into the system, like an offline reader
- Only power cabling required
- Available with integrated or remote reader
Controller - Intelligent door control

1-door controller
-
STC 1 P
The STC 1 P is a 1-door controller for electronic access control systems and access control. The STC 1 P itself has no reader ports or I/Os and must be operated together with the DCU 2 interface module. The DCU 2 provides the necessary reader port and I/Os for connecting the peripheral devices.
The DIN rail housing can be easily installed in the control cabinet or under the ceiling to save space. Modern and secure reading protocols such as OSDP or a transparent reader mode are supported. Own cryptology keys can also be used via a SIM card slot.
The STC 1 P is powered by PoE and is CloudReady and thus suitable for operation on-premise as well as via the cloud.
- Top-hat rail housing enables easy installation
- POE power supply
- CloudReady
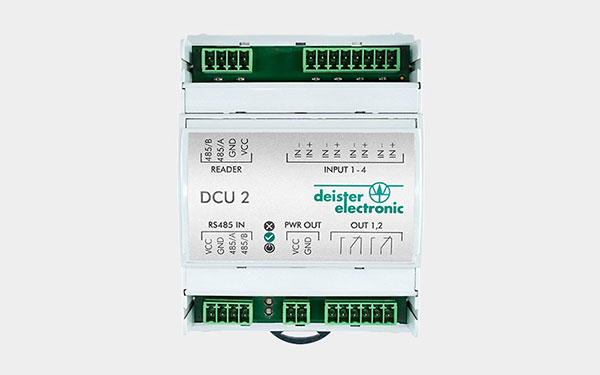
Interface module
-
DCU 2
The DCU 2 door control unit is an interface module for controlling a door. The DCU 2 can only be operated in conjunction with the STC 1 P.
The DCU 2 is equipped with four inputs, two of them designed as "Supervised Input", and two potential-free relay outputs.
The top-hat rail housing can be easily installed in the control cabinet or under the ceiling to save space. Modern and secure reader protocols such as OSDP or a transparent reader mode are supported.
- Top-hat rail housing allows easy installation
- 4x inputs, 2x supervised
- 2x relay outputs
- 1 RS485 reader port, max. two readers
- OSDP, OSDP crypt, deBus, deBus crypt

8-door controller
-
OCU 8
The OCU 8 is an 8-door controller for electronic access control systems and vehicle access control. The OCU 8 has 4x RS485 reader ports, to each of which up to two readers can be connected. It has 8x I/Os for connecting peripheral devices. The DIN rail housing can be easily installed in the control cabinet or under the ceiling to save space. Modern and secure reader protocols like OSDP or transparent reader mode are supported. Own cryptology keys can also be used via a SIM card slot. The OCU 8 is powered by an external power supply and can control additional readers or peripherals via expansion modules. The OCU 8 controller is CloudReady and thus suitable for operation on-premise as well as via the cloud.
- Top-hat rail housing enables easy installation
- CloudReady
- 8x I/Os
- 4 RS485 reader ports, max. 8 readers
- OSDP, OSDP crypt, deBus, deBus crypt
- 100.000 users can be managed
- 500.000 event buffers
- Can be extended by expansion modules

Reader extension module
-
OEU 8
The OEU 8 expansion module has four RS485 reader connections, eight potential-free relay outputs (four changeover and four make contacts) and eight digital, potential-free inputs. With this extension unit, the OCU 8 controller can be supplemented with the control option of up to eight additional doors.
The extension unit is automatically recognised by the Controller OCU 8. Via the built-in LEDs, the device status as well as the switching states of the inputs and outputs can be easily recognised on site, simplifying installation and commissioning.
- Easy installation
- Prepared for DIN rail mounting
- Adds four reader ports, eight digital inputs and eight relay outputs (four changeover and four make contacts) to the OCU 8 controller
- Includes all necessary I/Os and reader interfaces for controlling up to eight doors

Periphery expansion module
-
OEU 10/10
The OEU 10/10 expansion module has ten potential-free relay outputs with changeover contacts and ten digital, potential-free inputs. This extension unit can be used for a wide variety of applications, for example for integration in elevator systems. Thus, the OCU 10/10 can control up to ten floors of an elevator system per extension unit. The extension unit is automatically recognized by the OCU 8 controller. The device status and all switching states are indicated by LEDs. This simplifies installation and commissioning.
- Prepared for top hat rail mounting - Easy installation
- Adds ten digital inputs and ten relay outputs to the OCU 8 controller
- Includes all necessary I/Os for the control of elevator systems with up to ten floors
Ident media - The secure ID card

deister’s CipherCard
-
Secure card technology for modern businesses
The CipherCard is deister's highly secure access card that meets today's security and management requirements. The CipherCard provides highly secure encryption of access and user data, while offering flexibility for additional applications on our customers' cards.
- Highly secure 128 bit AES encrypted
- Based on MIFARE® DESFire technology
- Customized crypto keys
- Open for additional applications

Upgrade old cards
-
Cost-efficient transition to a secure future
We will gladly support you in transitioning from your existing access control system to our modern access control system. We can make the transition comfortable and seamless for your users by, for example, making our access control readers temporarily compatible with the existing ones and our new ID media. Once everyone has received a new ID card, the old technology is switched off at the click of a mouse - so together we can create a smooth transition to a secure future.
- Flexible readers that read old and new ID cards
- Advice and support for a seamless transition
Online control

-
High-quality and future-proof readers
Durable and updateableSecurity threats are constantly evolving. Technology is also constantly evolving to address the new threats - yet most companies continue to use their outdated access control technologies.
Switching to a new reading technology for access control creates concerns for many, as the effort is high and the technical hurdle seems complex. How much of the access control system needs to be replaced?
Can "old" credentials and "new" credential be used at the same time? Do all users and credentials have to be recreated and linked in the software? Will there be security gaps during transitioning to the new Icredentials? Is there a need for new crendentials at all?
We look back on over 30 years of experience in the development of access control readers and the use of card technologies. We still hold some of the basic patents of RFID technology and have implemented countless technology transitions. With our readers and project management, we have helped many international customers achieve secure access control technology.
Whether it's old 125 kHz formats, insecure credentials that only use MIFARE® Classic serial number or MIFARE® DESFire serial number, or other technologies such as CASI-RUSCO® , AWID or HID prox - we support you in transitioning to a more secure reading technology and offer high-quality readers that are future-proof and updateable.
Online Reader

Access control readers
-
One reader, all technologies
The timeless design provides a high-quality look and deister electronic's proven reading performance ensures fast and smooth operation. The readers are available in three different shapes to match the available space at the door. The reader's LEDs clearly indicate the status to the user. Even users with a red/green deficiency can recognise the status of the reader based on the LED positions. The readers feature a replaceable cover. Even after many years of use, you can make it look like brand new just by replacing the reader cover.
In addition to proven reading technologies such as MIFARE® Classic and MIFARE® DESFire, Bluetooth® and NFC™ are also supported. The readers have an open interface (Triple Technology™) to retrofit existing or future technologies, so you remain future-proof with the Infinity Readers™.
- Highest quality
- Low power consumption
- Remote firmware update
- Triple Technology™
- Available in two colours (Cosmic Black & Astral Grey)
- Interchangeable cover

Keypad readers
-
For cards and PINs
The keypad readers have a high-quality keypad with backlit keys and are available in three designs. The separately arranged LEDs clearly indicate the status to the user and the keypad provides haptic, visual as well as acoustic feedback. The reader's LEDs clearly show the status to the user. The keypad provides additional haptic, visual and acoustic feedback. Even users with a red/green deficiency can recognise the status of the reader based on the LED positions. The readers feature a replaceable cover. Even after many years of use, you can make it look like brand new just by replacing the reader cover.
Like the PRx access readers, the KPx keypad readers have an open interface (Triple TechnologyTM) to retrofit existing or future technologies.
- Highest quality
- Low power consumption
- Remote firmware update
- High-quality keypad with illuminated keys
- Triple TechnologyTM
- Available in two colours (Cosmic Black & Astral Grey)
- Replaceable cover

Flush-mounted readers
-
Our technology, your design
Our PRx 4 flush-mounted reader fits into any conventional flush-mounted box and can therefore be concealed. Whether you want to integrate it into other devices or install it with its own housing to match your design - there are no limits to your creativity.
- Highest quality
- Compact design suitable for conventional flush-mounted boxes
- Low power consumption
- Remote firmware update
- Triple TechnologyTM
Retrofit Security

Smart Cipher Box 1
-
Connecting link between controller and reader
The Smart Cipher Box 1 is installed between the access control reader and the controller. It transmits the security-critical process of decrypting credentials to a secure domain. The Smart Cipher Box 1 is usually installed close to the controller. This allows a very high level of security to be added to an existing access control system without having to replace the controller.
- Ideal for retrofitting
- More security without replacing existing controllers
- Security-critical decryption takes place in a secure domain

Smart Cipher Box 2
-
Connecting link between controller and reader
The Smart Cipher Box 2 can also transfer the security-critical decryption process of ID cards to a secure domain. In addition, the SBC has a SAM module installed to provide even more security and to be compliant with international standards.
- Ideal for retrofitting
- Integrated SAM module
Accessories

Reader Cover
- Want a design refresh?
Over time, the housing of the access control readers can become very worn, as the readers are usually installed for many years. You can easily replace the reader cover to make the reader look like new.
- Can be changed as often as desired
- Colour can be adapted
- Reader looks like new

MBL1
- Bluetooth
The MBL 1 is an attachable Bluetooth module that works together with the "deisterWallet" app. This means that every access reader can be equipped with Bluetooth even after installation. So you don't have to decide at the beginning of the project or equip only some of the doors for testing purposes.
- Flexible retrofitting
- Works together with the deisterWallet app
- Maximum flexibility in the rollout

Tamper plate
-
Each access reader has an internal tamper sensor. The board with an additional sensor can also be installed in order to specifically have the entire dismantling of the reader monitored by an alarm system.
- Flexible retrofitting
- Monitoring via an alarm system possible
Offline locking components
Offline reader

Electronic cylinder
-
Easy to upgrade
Just like a mechanical cylinder, the electronic cylinder can be installed in just a few steps. No drilling or other modifications to the door are required because the design is identical. The basic cylinder bodies can be ordered in five different installation lengths, including a half cylinder, and can also be adjusted in length directly during installation using spacers, meaning that the length can be adjusted in 5 mm steps from 30/30 to 45/75.
- Installation length can still be adjusted during installation
- Best quality - Made in Germany
- Fast reading speed

Electronic door fitting
-
Suitable for every door
The electronic fitting suits any door with its slim and simple design. The handle can be selected from four different models, depending on its use on solid or tubular frame doors. For mounting, the same drill holes as for a conventional fitting can be used.
The cover plate allows the parallel use of the existing cylinder for secure door locking or the elegant covering of the cylinder opening. The exchangeable cover plate allows adaptation to doors with different distances between handle and cylinder. The Digital Handle adapts perfectly to any door.
- Suitable for every door
- Slim and elegant design
- Additional mechanical locking cylinder (optional)
- Simple battery change

Electronic lock
-
Design meets security
The electronic motor lock has been developed for self-locking locks and combines security with design. The simple design can be discreetly combined with the design of the door handle and offers maximum freedom in the choice of shape and colour.
In addition, the electronic lock offers more security because neither damage nor forcible removal of the housing or electronics allows access to the lock mechanism inside the door.
- Maximum freedom for design
- More security
- Different designs to suit every door

Electronic cabinet lock
-
Secure storage of valuables in lockers or wardrobes - with the reliable and electronic locker and furniture lock from deister electronic. The elegant and timeless electronic lock does not require any cables, can be installed quickly and is easy to manage thanks to our Commander Connect software. Connecting the lock and integrating it into professional building and asset management software is therefore no problem at all.
- Available with different levers
- Attractive design, suitable for many office furniture, lockers and wardrobes
- Easy to assemble

Digital Safe
-
The battery-operated Digital Safe is a rugged key safe for outdoor and indoor use. Its weatherproof IP65 housing is suitable for any weather. The Digital Safe is opened contactlessly with an access card or via an app - the reading technology can be freely selected and all popular reading technologies such as MIFARE®, NFC™ or Bluetooth® are supported. This means that the Digital Safe can also be seamlessly integrated into an existing access control system and can be opened with the same credentials. The Digital Safe can also be flush mounted, providing the best possible mechanical protection. Weather impacts are also minimised by this type of installation.
- 70 mm diameter
- Enough space for ISO cards and large bunches of keys
- Independent of local IT infrastructure
- Standalone capable
- Weatherproof IP65 metal housing
- Content monitoring

WCU 2 Offline door control
-
Reader with integrated door control
The WCU 2 door control module is a reader with integrated inputs and outputs. It only requires a power supply, but is otherwise integrated into the system like an electronic cylinder.
Wherever an existing online reader is to be replaced and the functionality of an electronic cylinder is not sufficient, the WCU 2 is the ideal solution.
- Integration into the system, like an offline reader
- Only power cabling required
- Available with integrated or remote reader
Wireless connectivity

airLink® module
-
airLink® is a wireless solution for integrating digital locking components into the system. A clever energy management system ensures very low battery consumption. All data is secured with 128-bit AES encryption. Inside buildings, ranges of up to 30 m can be achieved, and outdoors up to 100 m.
- No cables required
- Transmission of real-time events
- Application based operating modes

airLink® USB stick
-
Using the wireless USB stick, the service software connects to the battery-operated readers. New devices can be configured or settings can be changed during operation.
- No driver required
- Configure and test devices directly on site
Long range readers
-
Automatic long-range vehicle identification
Fast, reliable and automatic long-range identification (AVI) identifies drivers and vehicles in all weather conditions. Queues in access and exit areas are eliminated. Ideally suited for car parks, traffic management and convenient access control. The technology can also be used in rail traffic, access-gated city centres, airports or toll roads. tranSpeed® integrates seamlessly with other control systems through many existing interfaces, but can also be used as a stand-alone solution. A wide selection of transponders is available, including robust heavy-duty transponders, self-adhesive labels for windscreens and ISO cards that perfectly combine two reading technologies.

Long-range readers - TSU 200
-
The TSU 200 is a compact and rugged long-range reader featuring an integrated antenna for passive UHF transponders. The water-protected housing allows for indoor and outdoor use.
With a range of up to 7 m, the TSU 200 is ideally suited for applications such as access control. Typical areas of application are multi-storey car parks, underground garages, car parks, access roads to company yards, etc.

Controller OCU 8
-
The OCU 8 access controller has 8x I/Os and can connect up to eight readers. Thus, it offers flexibility for controlling one or more driveways, each controlled by one or more readers.
In the event that identification at the entrance needs to be possible via UHF transponders and also access cards, UHF long-range readers and HF readers can be operated in parallel at the controller.
The top-hat rail housing is easy to install, and the compact dimensions offer many installation options.
- Connection of up to eight readers to 4x RS485 ports
- Combined operation of UHF wide range reader and HF reader
- Cloud ready
- Offline capability in case of network failures
Transponders

Bumper Tag
-
The UDC 160 / 170 is a passive UHF transponder with EPC Class 1 Gen 2 protocol. The antenna technology used allows it to be mounted directly on metal (on-metal transponder) and it can be read across a radius of 180°.
The wide reading angle and the reading range of up to 5 m are perfectly suited for applications in logistics, factory automation or vehicle identification. The UDC 160 / 170 is easy and quick to install on vehicles, containers, trains, etc. using screws or adhesive.

Windshield tag
-
The TPU 3082/92 is a passive UHF transponder for vehicle windscreens according to EPC Class 1 Gen 2 standard. These versatile transponders have been specifically designed for vehicle identification and are therefore excellent for e.g. car park or other long range applications. They are easy to apply to the windscreen. The optional vignette function of the TPU 3082/92 means that it cannot be removed without rendering the transponder unusable.
Various security functions are included to ensure data integrity and prevent copying of the transponders. If the maximum reading range of up to 6 m is not desired or is contra productive for the application, the RRD sticker for the TPU 3082/92 can be used to reduce the range to 66 % or 33 %.
Driver credential
-
Our Dual Technology credentials are the ideal solution when the driver and not the car is to be identified. The driver holds the transponder card into the reader´s direction and is thus conveniently identified without leaving the vehicle.
How and where the driver holds the credential often has a strong influence on whether it can be read reliably. Our special antenna design offers the world's best range and performance, no matter how the driver holds the credential.
In addition, it is a dual technology credential, supporting RFID technology for both the driveway and the doors in the building. So you only need one card for access to the premises and entering the building.
Vehicle locking system

-
Faster, Safer, More Comfortable
With vanLoxx a vehicle can be locked and operated safely. vanLoxx is an automatic door and vehicle control system designed to save time and ensure safety. Access to the driver's cab or the cargo area is only granted to the driver via a valid transponder or via the vehicle's own remote control.
With the vanLoxx solution, RFID readers are installed at the various doors. The driver simply presents his transponder to the corresponding reader and the motorized locking elements unlock the doors automatically. In the case of radio control via the ignition key or similar, the respective door unlocks when the unlocking function on the key is activated.
After leaving or entering the vehicle and the complete closing of the used door, the vanLoxx system automatically locks all accesses. If the vehicle is moved afterwards, e.g. because the tour is continued, doors that serve as rescue access in case of an accident can be unlocked again automatically.
- Time saving, the transponder is always on the wrist and is not plugged in
- No additional purchase of expensive keys in case of loss or defect
- Faster replacement of a transponder and vehicle remains productive
- Only the door the driver identifies himself with is opened
- More security due to automatic locking of the complete body
- Durable, designed for over 300,000 cycles
- Proven technology already in use on over 15,000 vehicles
Locking elements

Bascule lock
-
The bascule lock can be used preferably for double or single doors with two-point locking. It has a robust construction, which guarantees a long-lasting reliable function, even under rough conditions.
An LED indicator shows the status of the respective element and thus provides information on the operating status and function at any time. Each element is also assigned a door sensor, which monitors the status of the door.
- Durable and resilient
- Weatherproof
- Closes reliably
- Withstands rough handling

Deadbolt lock
-
At least one locking element is required for each vehicle. For example, the rear door, the partition door and the side door, which is mainly used to enter and exit the vehicle, can each be equipped with one locking element.
The locking elements have a robust design, which ensures long-term reliable operation, even under harsh conditions. Each element is equipped with a manual emergency release.
An LED indicator shows the status of the respective element and thus provides information on the operating status and function at any time. Each element is also assigned a door sensor, which monitors the status of the door.
- Durable and resilient
- Weatherproof
- Closes reliably
- Withstands rough handling
Control units

VBC 4 (driver terminal)
-
The driver terminal or controller is the heart of the installation. It controls and supplies all components connected via the system bus and thus takes over the sequence control of the projected system. The system can be configured, initialized and maintained without contact via the integrated RFID reader. Special programming cards are available for this purpose, which are individually assigned to the respective customer. This means that lost or defective transponders can be replaced quickly and the vehicle remains productive. In addition, the starting and stopping of a combustion engine, via buttons and/or the enabling and disabling of an electric drive can also be realized. Here, too, the RFID transponder, which is also used to unlock the doors, is used for secure operation. This provides a simple immobilizer that effectively prevents unauthorized use. The system is switched on and off with a key switch in the driver terminal. One has the choice between two modes.
- Automatic, here the locking system is active and works as required by the delivery application.
- Manual, here the locking system is switched off and one can operate the vehicle normally without the doors being locked automatically.

SPX 2 (RFID-reader)
- The external readers are located where a door on the vehicle must be unlocked in order to enter it. This can be the case, for example, at the passenger door, the side door of the cargo area, the rear door or in the interior of the vehicle. By presenting a transponder assigned to the vehicle, encrypted data is exchanged, which the system then uses to unlock the desired door. The LEDs show the current status.
Transponder
IDC 514 (ISO card)
- The IDC 514 ISO card transponder is used for administrative purposes and tests. It can be printed according to customer requirements and programmed accordingly.

IDC 507 (RFID-Fob)
- The IDC 507 is a transponder in the classic key fob form and is usually carried with other keys. The IDC507 is preferably used to unlock the vehicle.

IDC 517 (Bracelet transponder)
- The IDC 517 is a transponder that is attached to a wristband and typically worn on the wrist. This means that the driver does not necessarily have to have his hands free to trigger the unlocking process.
Protecting and monitoring
-
Online, offline and hybrid systems
As the inventor of electronic guard control and with over 30 years of experience, our dataLog® guard control system offers an extensive yet pragmatic range of functions. It helps you in the planning and monitoring of ongoing rounds and precinct runs, informs you via email or app about the status or events and automatically logs all services for you in clear reports.
The dataLog® system can be customized to meet your exact needs. The online app offers real-time functions and many advanced features for task planning and documentation. The guardiX II offline data collectors are child's play to operate without much training, are robust and have a very long battery life - ideal for simple, yet electronically monitored services.
The Commander Connect central management software offers many functions for round planning and precinct management. In addition, customizable reports can be generated tailor-made for own management or as proof of service.
- 125 kHz and NFC (also in mixed mode)
- Real-time features: round status, man down alarm
- Special features: Photo function with remarks, checklists, instructions
- Smartphone or data collector (also in combined operation)
- Extensive evaluation, customizable reports
Cloud-based systems

deisterCloud
-
Secure transfer of the data
The deisterCloud serves as a routing service for all smartphone data. All data in the cloud is always encrypted so that no security risk can arise.
Data can be transmitted in real time via the cloud. User logins and bidirectional exchanges from and to the user are possible at any time.
If the cloud connection is interrupted, the smartphone stores the data locally until the connection is re-established - the data is then synchronised losslessly so that nothing is lost and all time stamps are also recorded properly.
- Secure hosting in Germany
- No data loss even in case of connection failures
- Real-time data exchange

deisterCheckApp
-
The smartphone as a data collector
The deisterCheck app turns your smartphone into a data collector and supports your service staff. In addition to collecting the round, there are many other features, such as taking photos or filling out checklists, which can be used to enhance your service.
Furthermore, the deisterCheck app supports real-time features, such as man down alarm or tracking. Depending on your needs, these features can be activated and used.
- Facilitated round guidance with guidance support for personnel
- Real-time features such as emergency call, man down alarm, status updates
- Photo function with annotation
- Checklists, status selection, instructions, etc.
- Android compatible
Offline & Hybrid Solution

guardiX II
-
Robust data collector
Our guardiX II data collectors are characterised by their extremely handy and simple operation. They read RFID-based checkpoints without contact. The read data is provided with date / time and stored for later transmission and processing. Optical signals as well as vibration give the user immediate feedback on the successful detection of the respective checkpoint.
With their robust design without moving parts and IP67 certification, guardiX II data collectors are perfect for harsh environments and everyday use. Especially where patrols need to be carried out discreetly, or in noisy environments, vibration is a great advantage as feedback for the detection of a checkpoint. The excellent battery life with standard AA batteries results from the economical vibration function, which means that up to 500,000 checkpoints can be read with one set of batteries.
- Wear-free and contactless checkpoint detection
- Compatible with all previous deister electronic evaluation systems
- Very long battery life
- Robust design without moving parts
- Very easy to use, no extensive training necessary

guardTrans
-
Desktop readout station
The guardTrans is the readout station for all guardiX II data collectors. It is connected to the PC / laptop via the USB interface and transfers the acquired data after insertiing the data collector. The real-time clock in the guardiX II data collector as well as all other parameters are synchronized during the data download to ensure maximum accuracy for the rounds.
Audiovisual signals provide immediate feedback to the user about the data download.

guardiX Connect
-
Desktop readout station
No matter where you are, with the help of the guardiX Connect, the collected data can be transmitted to the control center immediately after each patrol. All you need is a power outlet or a USB port to power the guardiX Connect.
The data transfer is securely encrypted via a cellular communication module using the deisterCloud. This means you are completely independent of your customer's local infrastructure. In addition, the data always remains encrypted.

guardiX Connect
-
Additional round information
With the event cards, the security service provider can document additional events along the round. For example, it can be noted that a window is open or that a smoke detector is defective.
The security guard carries the event cards with him/her and can simply hold the corresponding card in front of the data collector when needed. According to the area of application, the significance and evaluation of the events is determined by the user of the system himself/herself.
- Simple operation
- Define own events
- Detailed documentation
Checkpoints
Checkpoints
-
125 kHz and NFC combined
Checkpoints store their information digitally in an RFID chip, which is read contactless by smartphone or data collector, avoiding the wear and tear of a checkpoint.
The checkpoints support two technologies: 125 kHz and NFC, ensuring that the dataLog system offers maximum compatibility. Old and new data collectors like guardix II as well as apps like the deisterCheck app can be used.
The small, inconspicuous plastic housing can either be glued or fixed with a special screw for more security. The checkpoints are insensitive to changing temperatures, weather, dirt and other environmental influences. Passive operation eliminates the need for a battery.
BabyGuard®
-
Reliable protection for newborns
The swapping or even abduction of newborns occurs time and again in maternity wards in hospitals. Even if the cases are usually solved quickly, the experience is traumatizing for everyone involved. The hospitals affected are confronted with a loss of reputation and financial damage.
The BabyGuard® solution provides full protection to ensure that babies can only leave supervised areas with authorized persons, such as parents or nurses. In case of unauthorized leaving of an assigned area, an alarm is immediately sent to the staff.
The system enables many other administrative functions, alarm options and automated reporting through integration with a hospital's nurse call system.
- Essential basic protection to prevent newborns from being switched or abducted
- Clear assignment of parents and newborns
- Monitored protection zones for reliable alerting of caregivers in case of separation of mother and child
- Uncomplicated use even with multiple births
Locator

LCA 500
-
The Locator LCA 500 is installed in the center of the zone to be monitored. This can be individual rooms or the passage area of a door. It transmits a permanent alarm signal in the LF frequency range at 125 kHz with an adjustable extension of approx. 1 - 5 m. Each alarm field is identified by a unique location code for communication with the amanTag® transponders located in the reading range of the locator. A UHF transceiver is integrated in the locator for bidirectional communication with the amanTag® transponders. The LCA 500 locator can be operated standalone or online.
- Comprehensive range of functions for effective baby protection
- Simultaneous identification of up to 10 persons
- Standalone and online operation
- Compact design
- Optional system configuration for alarm field extension and direction detection

LCA 500 ELA
-
Compared to the LCA 500, which is equipped with an integrated loop antenna for generating the alarm field at 125 kHz, the LCA 500 ELA has been designed for use with specified loop antennas, which are available in different design variants on site as door frame antennas, wall antennas or, in outdoor areas, as floor antennas. Antennas of this design allow a very precise definition and thus application-specific expansion of the wake-up field. The matching electronics integrated in the locator allow the connection of external loop antennas with a wide range of values of assigned inductances.
- Integration into and retrofitting of existing installations
- Concealed installation of the locator possible, e.g. in suspended ceilings
- Simple connection to loop antennas installed in the door, wall or floor area
Transponder

BTA 1
-
Baby transponder
The active BTA 1 Baby-Tag protects the newborn from abduction and swapping. During development, emphasis was placed on achieving minimal weight of the transponder while ensuring optimal performance, in order to avoid unnecessary burden on the newborn and guarantee the best possible protection. Without restricting freedom of movement, the tag can be worn in a diaper with an insert pocket. When entering the wake field of an amanTag® Locator, an alarm is triggered if the baby is not accompanied by its mother, an authorized caregiver, or nursing staff whose identification is associated with the baby tag through mother or companion transponders.
- Protection against abduction and mix-up
- Alarm when baby is unattended
- In-house locating of mother and baby

UTA 3
-
Mother transponder
The active UTA 3 mother transponder is used for authorized crossing and exiting of defined protection zones with an associated baby without triggering an alarm. If the corresponding BTA 1 baby transponder enters the wake field of an amanTag® Locator without the accompaniment of the UTA 3 mother transponder, an alarm is triggered. This effectively addresses the risk of abduction or swapping of newborns by providing immediate and reliable information to the nursing staff.
- Protection against abduction and mix-up
- Alarm when baby is unattended
- In-house locating of mother and baby

UTA 1
-
Mother and nurse transponder
The UTA 1 can be used as an alternative to the UTA 3 as a mother transponder and can also be worn by nursing staff in maternity wards. The additional push-button is used to trigger an assistance call incl. an area identifier while on the move, which is received within a radius of 25 m to generate an emergency call for immediate information of the nursing or security staff. The LED integrated in the UTA 1 is used to display a status message after pressing the push-button.
- Mobile emergency call to nursing and security personnel
- Feedback on successful transmission of the emergency call via integrated LED
- In-house location detection

ITA 3
-
Installer Transponder
The ITA 3 is a special transponder that can be used by staff from the areas of building management, service and maintenance. Thus, without the use of additional software, the extension of the wake-up area of a locator can be adapted to the concrete needs directly on site. For this purpose, the transponder has three buttons. A test call can be triggered via the large call button. The alarm field of the locator can be enlarged or reduced via the small buttons. An integrated LED indicates that the transponder is in the alarm field. Thus, the extension of a protection zone can be optimally set with this transponder and checked at regular intervals.
- Intuitive setting and checking of the alarm field expansion for defining a protection zone
- On-site configuration of the locator by service technicians without additional software
- Integrated LED for checking the expansion of the Locator alarm field
Runaway Protection Systems
-
Reliable protection for patients with mental illness
In nursing homes, taking care of disoriented residents with dementia poses a great challenge. The nursing goal is, on the one hand, to maintain and enhance the quality of life for as long as possible. On the other hand, due to the progressive and non-treatable symptoms of the disease, it is necessary to protect the affected people from danger through the targeted use of assistive technology.
The walk-away protection system SeniorGuard® was developed and optimised precisely for this purpose. It does not create physical barriers, but defines monitored movement zones in which free movement is possible for people with dementia. Leaving predefined protection zones leads to the immediate triggering of an alarm, which informs the responsible nursing staff in the form of an assistance call.
In addition, the SeniorGuard® system enables patients and caregivers to make mobile emergency calls to summon help as quickly as possible in dangerous situations.
- Runaway protection for dementia patients
- Relief of the organizational workflow in care facilities
- Monitored protection zones for reliable alerting of nursing personnel
- Localization of the whereabouts
Locator

LCA 500
-
The Locator LCA 500 is installed in the center of the zone to be monitored. This can be individual rooms or the passage area of a door. It transmits a permanent alarm signal in the LF frequency range at 125 kHz with an adjustable extension of approx. 1 - 5 m. Each alarm field is identified by a unique location code for communication with the amanTag® transponders located in the reading range of the locator. A UHF transceiver is integrated in the locator for bidirectional communication with the amanTag® transponders. The LCA 500 locator can be operated standalone or online.
- Comprehensive range of functions for effective baby protection
- Simultaneous identification of up to 10 persons
- Standalone and online operation
- Compact design
- Optional system configuration for alarm field extension and direction detection

LCA 500 ELA
-
Compared to the LCA 500, which is equipped with an integrated loop antenna for generating the alarm field at 125 kHz, the LCA 500 ELA has been designed for use with specified loop antennas, which are available in different design variants on site as door frame antennas, wall antennas or, in outdoor areas, as floor antennas. Antennas of this design allow a very precise definition and thus application-specific expansion of the wake-up field. The matching electronics integrated in the locator allow the connection of external loop antennas with a wide range of values of assigned inductances.
- Integration into and retrofitting of existing installations
- Concealed installation of the locator possible, e.g. in suspended ceilings
- Simple connection to loop antennas installed in the door, wall or floor area
Transponder

UTA 2
-
Patient transponder
The UTA 2 transponder is particularly used for patients with dementia. If a patient with a tendency to wander enters an area monitored by the locator's transmission field, an alarm will be immediately triggered to inform the nursing staff promptly. The system can be configured to prevent alarms from being triggered when a patient, accompanied by nursing personnel, enters specific monitoring areas, such as on the way to therapy. The transponder is equipped with a sticker resembling a wristwatch, designed to create the impression of an inconspicuous and familiar object, especially for patients with dementia.
- Effective protection for patients with dementia
- Unobtrusive wristwatch design with clock face
- In-house location tracking

UTA 3
-
Patient transponder
The UTA 3 transponder is used as a patient tag, but it can also be used as an alternative to the UTA 2 transponder for individuals with dementia. If a patient with a tendency to wander enters an unauthorized area monitored by a locator, an alarm will be triggered, allowing the nursing staff to respond promptly. It is also possible to configure the system so that no alarm is triggered when an authorized companion is present. The wristband transponder features a discreet design and offers a high level of comfort when worn.
- Effective safeguarding for patients with dementia
- Subtle and inconspicuous design
- In-house location tracking

UTA 1
-
Patient and nursing transponder
The UTA 1 can be used as an alternative to the UTA 3 as a patient transponder and can also be worn by staff on nursing stations. The additional push-button is used to trigger an assistance call incl. an area identifier while on the move, which is received within a radius of 25 m to generate an emergency call for immediate information of the nursing or security staff. The LED integrated in the UTA 1 is used to display a status message after pressing the push-button.
- Mobile emergency call to nursing and security personnel
- Feedback on successful transmission of the emergency call via integrated LED
- In-house location determination

ITA 3
-
Installer Transponder
The ITA 3 is a special transponder that can be used by staff from the areas of building management, service and maintenance. Thus, without the use of additional software, the extension of the wake-up area of a locator can be adapted to the concrete needs directly on site. For this purpose, the transponder has three buttons. A test call can be triggered via the large call button. The alarm field of the locator can be enlarged or reduced via the small buttons. An integrated LED indicates that the transponder is in the alarm field. Thus, the extension of a protection zone can be optimally set with this transponder and checked at regular intervals.
- Intuitive setting and checking of the alarm field expansion for defining a protection zone
- On-site configuration of the locator by service technicians without additional software
- Integrated LED for checking the expansion of the Locator alarm field
Access Control

Digital Handle
-
Intuitive access control for living spaces and living areas
Electronic door opening systems represent a widespread technical solution for gaining access to secured areas or private rooms by carrying credentials, e.g. in the form of transponders or chip cards. The Digital Handle was designed especially for use in care facilities with regard to residents with physical and mental disabilities.
The electronic door fitting enables a door to be opened without explicit presentation of the necessary credential. Carrying an active transponder, which can be worn on the wrist for example, is sufficient to allow authorised persons access to protected areas and residential rooms. The door fitting is equipped with a motion detector that activates the integrated amanTag® reader when a person approaches. The reader evaluates the information of an amanTag® transponder so that a person with the appropriate authorisation is granted access.
- Barrier-free access to residential rooms
- Intuitive handling due to hands-free concept
- Can be used with active amanTag® transponders as well as passive cards or transponders
- Compatible with airlLink wireless technology
- More security for residents and staff

airLink® module
-
The ALS 20 airLink® module is designed to network the door release elements distributed in the building via radio. It can be operated in a frequency band with 100% duty cycle, a high data rate and low transmission power as well as in a band with only 1% duty cycle, a low data rate but high transmission power and thus a large range. The main application areas of the ALS 20 are the registration of all online bookings of the digital cylinders and fittings present in the reception area. In addition, the radio technology enables wireless synchronization of all clocks in the system network, management of blacklist entries and transmission of battery status messages to the central management software Commander Connect.
- Wireless networking for electronic door opening systems
- Secure communication through AES data encryption
- Modular expansion of network coverage
Auto-identification
-
Reliable identification for transparent processes in the digital enterprise
Industrial processes in the digital enterprise require complete transparency and a high degree of individualization. Our RFID solutions effectively connect the physical world with digital systems, unlocking new automation potentials throughout the entire production and supply chain. Whether you need flexible production control, efficient asset management, reliable traceability of products and components, or intelligent synchronization of your supply chain, deister electronic, as an innovative provider, delivers a comprehensive and scalable RFID product portfolio in the field of secure identification and automation solutions.
Our universally integrable products offer the perfect solution for every application and requirement, enabling the identification and digitization of goods and transport assets using RFID. As a long-standing specialist in RFID technology, we support all frequencies (LF, HF, and UHF) and provide assistance for integration into your own automation systems.
Passive HF RFID reader
RDK 1
- The compact 13.56 MHz RDK 1 ISO read/write module with integrated antenna is ideally suited for integration in mobile equipment, human/machine user interfaces, medical devices or even printers due to its miniaturized design. Module variants are available with remote antenna and customer-specific software.

RDL 150 T
-
HF reader
Unique ETF developed by deister electronic. The technology – "Easy Trim Function" – makes it possible to quickly calibrate the reader to suit different environmental conditions. All it takes is a few settings and the RDL 150 T is set to the best-possible reading distance within seconds of being installed. The reader is designed for use in "Track and Trace" applications. Goods inwards inspections and dispatch or tracking production processes and quality assurance: the RDL 150 T is the right solution wherever multiple transponders need to be reliably read and written simultaneously at changing distances. Due to its compact design and integrated antenna this reading system is ideally suited for renting out processes, tracking documentation and for high-speed identification purposes. Equipped with a trigger input and a switching output as well as extensive configuration options the RDL 150 T fully satisfies widely diverging requirements.
- Adaptable for different installation locations
- Easy to install thanks to compact, flat housing with integrated antenna
- Read and write functions in a single device
- Suitable for outdoor applications
- Updateable software
- Digital I/Os as control inputs and control outputs

RDL 90 / RDL 90 T
-
The RDL 90 is designed for short read/writing distances. Consequently, it offers an optimum solution for most applications in industrial automation. Its small housing dimensions ensure it can also be installed where the effective use of limited space is critical. Depending on the application it is possible to both read from and write data to transponders. For example, it is possible to use associated product information without the need to access a central database. Equipped with a trigger input and a switching output as well as extensive configuration options this reader is able to fulfil the many requirements demanded in factory automation applications. The rugged design and encapsulated electronics of this reader are ideally suited for harsh environments.
- Anti-collision, simultaneously detect more than one transponder in the field
- Read and write functions in a single device
- Updateable software
- Extensive configuration options
- RDL 90 T offers digital I/Os as
control inputs and control outputs - Rugged, fully encapsulated design
Passive UHF RFID reader
TSU 200
-
UHF reader
The TSU 200 is a compact and rugged long-range reader featuring an integrated antenna for passive UHF transponders. The water-protected housing allows for indoor and outdoor use.
With a range of up to 7 m, the TSU 200 is ideally suited for applications such as access control. Typical areas of application are multi-storey car parks, underground garages, car parks, access roads to company yards, etc.
HF & UHF transponder

RDC 50 M
-
The passive RF disk transponders have been explicitly developed for harsh environments (IP67) and are particularly robust and durable. In addition, there are special on-metal transponders encapsulated in the housing, which have been designed for mounting on metal and achieve optimum ranges.
The transponders have high data rates for fast identification, high read and write ranges and are ideally suited for use in logistics, automation, on vehicles and for outdoor use.

IDC 100 M
-
The passive RF disk transponders have been explicitly developed for harsh environments (IP67) and are particularly robust and durable. In addition, there are special on-metal transponders encapsulated in the housing, which have been designed for mounting on metal and achieve optimum ranges.
The transponders have high data rates for fast identification, high read and write ranges and are ideally suited for use in logistics, automation, on vehicles and for outdoor use.

UDC 160
-
The passive RF disk transponders have been explicitly developed for harsh environments (IP67) and are particularly robust and durable. In addition, there are special on-metal transponders encapsulated in the housing, which have been designed for mounting on metal and achieve optimum ranges.
The transponders have high data rates for fast identification, high read and write ranges and are ideally suited for use in logistics, automation, on vehicles and for outdoor use.

UDC 70
- The passive UHF transponders are robust, durable and have been explicitly designed for the harsh environment (IP67) in industry. In addition, they are also ideally suited for mounting on metal. With the large reading angle and long range, they are ideally suited to applications in logistics, factory automation, vehicle identification, etc.
LF/HF and UHF desk reader

RDL 5
- The table readers enable easy assignment of transponders to the control system. The table readers equipped with LF/HF and UHF technology can be connected to a PC via USB interface. Other areas of application are serialization and writing of transponders, POS applications and teach-in processes.

UDL 5
- The table readers enable easy assignment of transponders to the control system. The table readers equipped with LF/HF and UHF technology can be connected to a PC via USB interface. Other areas of application are serialization and writing of transponders, POS applications and teach-in processes.
Waste Management
-
The intelligent solution in waste identification
The waste disposal and recycling industry has embraced Industry 4.0 technologies through automated vehicles, smart waste containers, and efficient recycling facilities. The use of chipped waste bins, mobile applications, and software solutions for route optimization facilitates daily operations, making processes faster, more transparent, and efficient. Resource conservation, as well as time and cost savings, are the main focus.
On-board computers, identification systems, and efficient weighing areas form the standard repertoire of a modern waste management company, providing cost and performance transparency to consumers and waste disposal companies. They also provide important incentives for waste prevention and the separation of valuable resources.
The increasing connectivity through waste apps and smart bins significantly drives demand-oriented waste disposal, leading to more efficient processes and improved planning security. This strengthens the competitiveness of companies and offers new growth opportunities. Digital documents will shape the future of waste management, and the digitization of waste disposal continues to progress.
Benefits for waste disposal companies and municipalities:
- Transparency in logistics and finances
- Cost savings / proof of disposal
- Expansion of services
- Only paid services are fulfilled (blacklist)
- Secure investments through modular construction
- Cost and performance transparency to consumers and waste disposal companies
- Easier information provision to consumers
- Prevention of unauthorized waste disposal
- Improved acceptance of notifications
- Analysis for future fees Incentives for waste prevention and guidance for the separation of valuable resources
LFR 4 universal reader
-
LF reader for BiTech® antennas
The LFR 4 reads disposal containers with HDX and FDX transponders, identifying transponder numbers and antenna identifiers. The captured data is transferred to tablets or the onboard computer.
The auto-trim function ensures quick installation and immediate system readiness. Up to 4 antennas can be connected if needed. The auto-trim function allows for the mixed use of various tooth and body antennas.
The reader is designed for rugged use and is resistant to electrical interference and metallic environments.

THH handheld
-
LF, HF, UHF & Barcode Data Collection
The Quadro Handheld is the latest generation of rugged handheld scanners. It features LF, HF, and UHF reading technologies, making it the ideal all-rounder for daily work tasks.
Optionally, a fourth reading technology, a QR/barcode scanner, can be retrofitted. The data can be effortlessly read out via USB, Bluetooth®, or airLink® interfaces. A special vehicle mount is available for use in vehicles.

TSU 200 long-range reader
-
Long-range, robust design, IP67
The TSU readers impress with their robust aluminum die-cast housing in a compact design. The reader and antenna are integrated into a single housing, perfectly calibrated at the factory.
The reader features an integrated auto-trim function, which optimizes the range up to 7m depending on the placement and orientation of the transponders. The operating status is indicated by a highly visible LED display. All connections on the reader are designed as M12 connectors.
Antennas
AZF tooth antenna
-
Perfect reading range, direct mounting
The tooth antenna has a reading range of up to 5 cm and offers high mechanical stability with stainless steel protectors and glass-fiber reinforced material. By mounting directly on the comb structure, the installation location is predefined.
The tooth antenna ensures fast and reliable reading of HDX or FDX transponders, regardless of the lifter or containers.
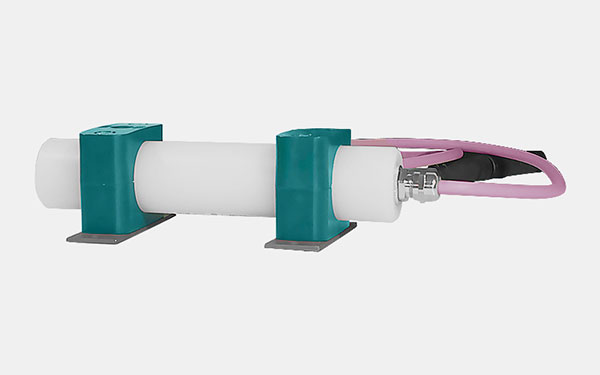
ABF body antenna
-
Reliable detection, optimal reading range
All disposal containers with HDX and FDX transponders are identified quickly and reliably.
When combined with the LFR 4 reader with auto-trim function, it ensures quick installation and immediate system readiness. The reading range of up to 20 cm, when used with the TBF 134 transponder, is ideal for identifying plastic or metal containers.
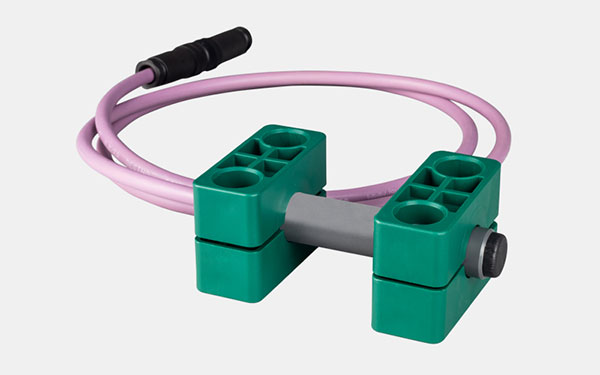
ASF Rear Comb Antenna
-
Superior Reading Performance in a Compact Design
The rear comb antenna can be seamlessly mounted on the comb structure, making it the ideal solution when installing a tooth antenna is not possible. With the ASF rear comb antenna, containers of various sizes can be easily attached and read, whether they are rear loaders or side loaders.
Transponders

TCX 134
-
Chipnest transponder
Der BDE-compliant TXC 134 transponder has been specifically designed for chipnest mounting. Its features allow for reliable identification with both built-in readers on waste collection vehicles and handheld devices.
The transponder can be easily screwed or pressed into the designated chipnest, enabling quick installation even on filled containers. With its rugged and compact construction, the TCX 134 is maintenance-free and resistant to impacts and shocks.

TBF 134
-
Reliable on metal
Designed for mounting on metal, the TBF 134 transponder allows for reliable identification of metal containers, unlike the TSF 134.
Built to withstand impacts and shocks, this rugged and compact transponder offers superior durability. When working with metallic containers, the TBF 134 is the right choice.

UDC 70
-
Passive UHF transponder
The UDC series transponders are known for their exceptional durability and longevity, even in harsh operating conditions. These passive UHF transponders are specifically designed for applications in vehicle identification, container management, logistics, and process automation.
Both the UDC 70 and the UDC 70 M, designed for mounting on metallic surfaces, are equipped with transponder inlays that enable optimized reading range and a large detection area.
Software overview

Commander Connect
-
One software, all systems
Manage users, doors, accesses, keys, valuables and your resources in their very own way and increase the efficiency and security of your operations and their management.
You can manage all deister systems across solutions with the central Commander Connect software. The comprehensive reporting system offers predefined freely configurable custom reports to suit your own requirements.
Workflows allow the automation of the system and offer endless possibilities to freely link different software functions, but also hardware functions.
- Client/Server Architecture
- One software for all deister systems
- Extensive reporting
- Workflows and other powerful automation features
- Extensive integrations to other software solutions
Deister cockpit
-
Secure and tailored to your requirements
The deisterCockpit is intuitive to use and easy to configure. Start as if on a blank sheet of paper and build your very own version of the deisterCockpit completely freely from a variety of widgets.
And it doesn't have to stay with one cockpit - each user can have his own cockpit or use several cockpits in parallel, each individually adapted to the rights level and the application.
If the framework conditions change, you can also easily adapt your deisterCockpit. It is as flexible and agile as the world of today and tomorrow, so it always fits your requirements.
- 100% adaptable to your requirements
- Contents are displayed according to user rights
- Any number of cockpits are possible, each one suitable for the application


